-
Posts
2,544 -
Joined
-
Last visited
Posts posted by trium
-
-
ff v85.0.1
5. feb 2021
Fixed
-
Prevent access to NTFS special paths that could lead to filesystem corruption.
-
Fixed a crash when authenticating to websites using SPNEGO on macOS devices with Apple Silicon CPUs (bug 1685427).
-
Avoid printing an extra blank page at the end of some documents (bug 1689789).
-
Fixed a browser crash in case of unexpected Cache API state (bug 1684838).
-
Fixed external URL scheme handlers when using the Firefox flatpak (bug 1688966)
-
firefox legacy v1.16.4.28
JustOff released this
Jan 25, 2021
Change
- Backport several improvements and fixes from the upstream (thanks to @hawkeye116477)
- Update and add new scriptlets and resources from the upstream
- Fix svg icons in redesigned dashboard on Gecko 45-51
-
firefox legacy v1.16.4.27
JustOff released this
Dec 21, 2020
Change
- Backport several improvements and fixes from the upstream (thanks to @hawkeye116477)
-
Update and add new scriptlets from the upstream
- addEventListener-defuser.js / aeld
- addEventListener-logger.js / aell
- cookie-remover.js
- google-analytics.com/analytics.js
- json-prune.js
- no-setInterval-if.js / nowoif
- no-setTimeout-if.js / nostif
- set-constant.js / set
- twitch-videoad.js
- window.open-defuser.js / nowoif
- abort-on-stack-trace.js / aost (new)
- no-fetch-if.js (new)
-
-
ublock v1.32.2
github-actions released this
Dec 25, 2020
Closed as fixed:
Core
Notable commits without en entry in the issue tracker
-
ublock v1.32.0
github-actions released this
Dec 22, 2020
New:
Ability to launch element picker into embedded frames, through a new "Block element in frame..." entry in the contextual menu.
Support for
match-casefilter option, but only for regex-based static network filters.Ability to auto-complete (Ctrl-Spacebar) hostname values for origin-related options in static filter editor according to currently opened tabs.
Changes:
Dynamic filtering
Noop-ing a blocked 3rd-party cell will cause uBO to immediately attempt to reload blocked stylesheets, if any. This will also occurs when the noop-ing is done through the "relax blocking mode" shortcut, in which case uBO will no longer force a reload the whole page. You can restore the previous behavior by modifying the advanced setting
blockingProfiles.Closed as fixed:
Core
- GitHub dark mode makes whole page invisible when element picker is active
- :watch-attr() stopped working (regression in 1.30.0)
-
uBO should ignore
redirect=directives with unrecognized redirect token - Can't load the images
- Reverse lookup partially fails for a filter redirecting to empty media resource
- Add AdGuard's "$removeparam" as an alias for "$queryprune"
- Network error entries in the logger are no longer colored in red
- Support parsing "Homepage:" list header for custom lists
- Please change the dashboard icon to a gear
- Improve source & destination sorting in "My rules" settings pane
- uBO badge counter doesn't work when network requests originate from service-workers
- Convert "$rewrite=abp-resource" into "$redirect"
- Migrate icons to FontAwesome svg files (from the font file)
- Element picker works incorrectly on mail.com
Notable commits without en entry in the issue tracker
-
ublock v1.31.2
gorhill released this
Dec 3, 2020
This minor release benefits Chromium-based browsers. Chromium 87 added the long time missing
tabs.removeCSS()API, which uBO uses:- To enable the real-time toggling of cosmetic filters through the no-cosmetic-filtering switch;
- To enable visualization of hidden elements in DOM inspector.
But the call to
tabs.removeCSS()was still failing in uBO due to Chromium being more strict regarding the arguments passed to the API.Closed as fixed:
Commit with no entry in issue tracker:
-
ff v78.7.0 esr
26. jan 2021
Fixed
-
Various stability, functionality, and security fixes
QuoteSecurity Vulnerabilities fixed in Firefox ESR 78.7
- Announced January 26, 2021
- Impact high
- Products Firefox ESR
- Fixed in
-
- Firefox ESR 78.7
#CVE-2021-23953: Cross-origin information leakage via redirected PDF requests
- Reporter Rob Wu
- Impact high
Description
If a user clicked into a specifically crafted PDF, the PDF reader could be confused into leaking cross-origin information, when said information is served as chunked data.
References
#CVE-2021-23954: Type confusion when using logical assignment operators in JavaScript switch statements
- Reporter Gary Kwong
- Impact high
Description
Using the new logical assignment operators in a JavaScript switch statement could have caused a type confusion, leading to a memory corruption and a potentially exploitable crash.
References
#CVE-2020-26976: HTTPS pages could have been intercepted by a registered service worker when they should not have been
- Reporter Andrew Sutherland
- Impact moderate
Description
When a HTTPS page was embedded in a HTTP page, and there was a service worker registered for the former, the service worker could have intercepted the request for the secure page despite the iframe not being a secure context due to the (insecure) framing.
References
#CVE-2021-23960: Use-after-poison for incorrectly redeclared JavaScript variables during GC
- Reporter Irvan Kurniawan
- Impact moderate
Description
Performing garbage collection on re-declared JavaScript variables resulted in a user-after-poison, and a potentially exploitable crash.
References
#CVE-2021-23964: Memory safety bugs fixed in Firefox 85 and Firefox ESR 78.7
- Reporter Mozilla developers and community
- Impact high
Description
Mozilla developers Alexis Beingessner, Christian Holler, Andrew McCreight, Tyson Smith, Jon Coppeard, André Bargull, Jason Kratzer, Jesse Schwartzentruber, Steve Fink, Byron Campen reported memory safety bugs present in Firefox 84 and Firefox ESR 78.6. Some of these bugs showed evidence of memory corruption and we presume that with enough effort some of these could have been exploited to run arbitrary code.
References
-
-
on my portable v5.75 is not a file "ccupdater..." also not with internetaccess and also is not create a task.
-
ff v84.0.1
22. dec 2020
Fixed
-
Fixed problems loading secure websites and crashes for users with certain third-party PKCS11 modules and smartcards installed (bug 1682881).
-
Fixed slower than expected performance and flickering on Canvas elements for some Windows users (bug 1683116).
-
Fixed a bug causing some Unity JS games to not load on Apple Silicon devices due to improper detection of the OS version (bug 1680516).
-
Fixed crashes caused by various third-party antivirus software.
-
-
Merry Christmas, relaxed, happy and satisfied holidays and a good Christmas dinner :-)
-
ff v78.6.0 esr
15. nov 2020
Fixed
-
Various stability, functionality, and security fixes
QuoteSecurity Vulnerabilities fixed in Firefox ESR 78.6
- Announced December 15, 2020
- Impact critical
- Products Firefox ESR
- Fixed in
-
- Firefox ESR 78.6
#CVE-2020-16042: Operations on a BigInt could have caused uninitialized memory to be exposed
- Reporter André Bargull
- Impact critical
Description
When a BigInt was right-shifted the backing store was not properly cleared, allowing uninitialized memory to be read.
References
#CVE-2020-26971: Heap buffer overflow in WebGL
- Reporter Omair, Abraruddin Khan
- Impact high
Description
Certain blit values provided by the user were not properly constrained leading to a heap buffer overflow on some video drivers.
References
#CVE-2020-26973: CSS Sanitizer performed incorrect sanitization
- Reporter Kai Engert
- Impact high
Description
Certain input to the CSS Sanitizer confused it, resulting in incorrect components being removed. This could have been used as a sanitizer bypass.
References
#CVE-2020-26974: Incorrect cast of StyleGenericFlexBasis resulted in a heap use-after-free
- Reporter Pham Bao of VinCSS (Member of Vingroup)
- Impact high
Description
When
flex-basiswas used on a table wrapper, aStyleGenericFlexBasisobject could have been incorrectly cast to the wrong type. This resulted in a heap user-after-free, memory corruption, and a potentially exploitable crash.References
#CVE-2020-26978: Internal network hosts could have been probed by a malicious webpage
- Reporter Samy Kamkar, Ben Seri, and Gregory Vishnepolsky
- Impact moderate
Description
Using techniques that built on the slipstream research, a malicious webpage could have exposed both an internal network's hosts as well as services running on the user's local machine.
References
#CVE-2020-35111: The proxy.onRequest API did not catch view-source URLs
- Reporter Yassine Tioual
- Impact low
Description
When an extension with the proxy permission registered to receive
<all_urls>, the proxy.onRequest callback was not triggered for view-source URLs. While web content cannot navigate to such URLs, a user opening View Source could have inadvertently leaked their IP address.References
#CVE-2020-35112: Opening an extension-less download may have inadvertently launched an executable instead
- Reporter Samuel Attard via the Chrome Security Team
- Impact low
Description
If a user downloaded a file lacking an extension on Windows, and then "Open"-ed it from the downloads panel, if there was an executable file in the downloads directory with the same name but with an executable extension (such as .bat or .exe) that executable would have been launched instead.
Note: This issue only affected Windows operating systems. Other operating systems are unaffected.References
#CVE-2020-35113: Memory safety bugs fixed in Firefox 84 and Firefox ESR 78.6
- Reporter Christian Holler
- Impact high
Description
Mozilla developer Christian Holler reported memory safety bugs present in Firefox 83 and Firefox ESR 78.5. Some of these bugs showed evidence of memory corruption and we presume that with enough effort some of these could have been exploited to run arbitrary code.
References
-
-
ff v78.4.1 esr (belated)
10. nov 2020
Fixed
QuoteSecurity Vulnerabilities fixed in Firefox 82.0.3, Firefox ESR 78.4.1, and Thunderbird 78.4.2
- Announced November 9, 2020
- Impact critical
- Products Firefox, Firefox ESR, Thunderbird
- Fixed in
-
- Firefox 82.0.3
- Firefox ESR 78.4.1
- Thunderbird 78.4.2
#CVE-2020-26950: Write side effects in MCallGetProperty opcode not accounted for
- Reporter 360政企安全漏洞研究院 in Tianfu Cup 2020 International Cybersecurity Contest
- Impact critical
Description
In certain circumstances, the MCallGetProperty opcode can be emitted with unmet assumptions resulting in an exploitable use-after-free condition.
References
-
ff v84.0
15. dec 2020
New
-
Native support for macOS devices built with Apple Silicon CPUs brings dramatic performance improvements over the non-native build that was shipped in Firefox 83: Firefox launches over 2.5 times faster and web apps are now twice as responsive (per the SpeedoMeter 2.0 test). If you are on a new Apple device, follow these steps to upgrade to the latest Firefox.
-
WebRender rolls out to MacOS Big Sur, Windows devices with Intel Gen 6 GPUs, and Intel laptops running Windows 7 and 8. Additionally we'll ship an accelerated rendering pipeline for Linux/GNOME/X11 users for the first time, ever!
-
Firefox now uses more modern techniques for allocating shared memory on Linux, improving performance and increasing compatibility with Docker.
-
Firefox 84 is the final release to support Adobe Flash.
Fixed
-
Various security fixes
Enterprise
-
Various bug fixes and new policies have been implemented in the latest version of Firefox. You can see more details in the Firefox for Enterprise 84 Release Notes.
Developer
-
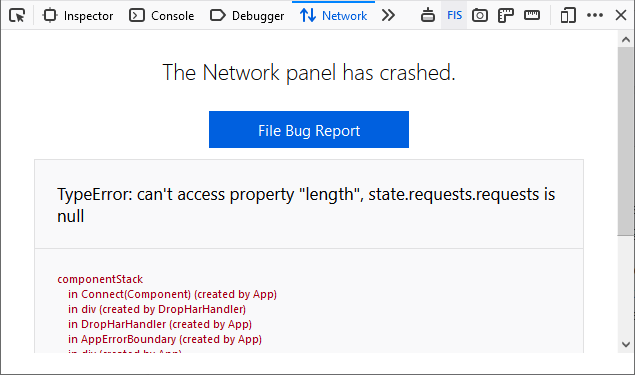
The Network panel is now able to handle unexpected crashes and render useful debugging details such as a related stack-trace. Users can also easily file a bug report by clicking on the available link to help improve the stability of the tool.
-
The Accessibility Panel now includes an option for displaying elements in their tabbing order in order to help developers see what elements are focusable when tabbing and in what sequence.
unresolved
-
macOS users running on Apple Silicon systems may encounter playback errors on encrypted content if the Rosetta system software is not installed.
-
macOS users running Cylance antivirus software may see their Firefox installation get corrupted due to being erroneously flagged as malware.
-
-
-
today it works fine for me too...
perhaps the hard working helpers just need a little bit longer now and then :-) thanks
-
hi fans,
the headline v5.75
but in the text v5.74
the next bug:
i mean this doesnt work
https://www.ccleaner.com/knowledge/ccleaner-v5758238
QuoteFehler: Umleitungsfehler
Die aufgerufene Website leitet die Anfrage so um, dass sie nie beendet werden kann.
Dieses Problem kann manchmal auftreten, wenn Cookies deaktiviert oder abgelehnt werden.
QuoteError: redirect error
The accessed website redirects the request so that it can never be completed.
This problem can sometimes occur when cookies are disabled or refused.
-
-
firefox legacy v1.16.4.26
gorhill released this
Oct 26, 2020
Change
- Make the button look consistent in Pale Moon on Windows
- Fix regression regarding filter used count per list
-
Backport several improvements and fixes from the upstream (thanks to @hawkeye116477)
- Add no scripting feature
- Warn when navigating away from pane with unsaved changes
- Select existing "Advanced settings" page if any
- Update links for docs
- Fix problems with search input readability
-
Visually emphasize directive syntax (
!#if/!#endif) in list viewer/editor - Allow to view list content from blocked-document page
- Fix filterlists and my filters wrapping
- Make use of CodeMirror in "Advanced settings" page
- Update urlhaus-filter URL
-
ublock v1.31.0
gorhill released this
Nov 17, 2020
Notes
The format of compiled filter lists has changed, this means that when you will be updated to 1.31.0, uBO will have to parse and compile all your enabled filter lists, which may cause larger than usual delay at first launch following update to 1.31.0. This is a one time event.
New:
Click-to-load
Support to replace embedded frames with a click-to-load widget. Examples of usage:
||youtube.com/embed/$3p,frame,redirect=click2load.html ||scribd.com/embeds/$3p,frame,redirect=click2load.html ||player.vimeo.com/video/$3p,frame,redirect=click2load.htmlResult:
Users of medium mode can experiment with a redirect rule to reveal embedded frames in a page:
*$3p,frame,redirect-rule=click2load.htmlOr if you want to have click-to-load only for embedded widgets from specific origins being blocked (reminder:
redirect-ruledoes not create a block filter):||youtube.com/embed/$3p,frame,redirect-rule=click2load.htmlChanges:
Resources redirected to local, neutered versions will no longer be collapsed as would occur if those resources were only blocked. This change is to enable implementation of the new click-to-load feature.
Cloud storage compression is now enabled by default.
Interactivity for the no-large-media-elements switch has been improved. Notably, when the switch is enabled, uBO will try to stop playback of
blob:-based media elements.Closed as fixed:
Firefox for Android
Core
- "Home" button on Strict blocking page works incorrectly in some cases
- Implement a version of "{{origin}}" that uses the whole URL and not just the domain
-
cosmetic filter
## selectoris valid in element picker only -
Implement
$querypruneparameter - Calling callback if provided for google analytics mock
- Redirection syntax issue
- Use user styles to collapse the placeholder of blocked resources
- Make load-on-demand smarter for blocked large media elements
Notable commits with no entry in issue tracker:
-
Work around Firefox's
data:favIconUrl leak - Make json-prune scriptlet also trap Response.json() calls
- Incrementally improve static filtering parser
- Coallesce origin hit filters into their own bucket
-
Re-classify
redirect=option as a modifier option - Improve token extraction from regex-based filters
- Improve specificity slider in element picker
- Use a CodeMirror editor instance in element picker
- Add support for click-to-load of embedded frames
- Minor improvements to syntax highlight of static filters
-
ublock v1.30.10
gorhill released this
Nov 16, 2020
Not for publication: this release exists strictly as reference point for future releases of uBO for development purpose.
The built-in benchmark of the static network filtering engine has been fine tuned such that the benchmark results in the current iteration can be used as reference against future versions of uBO.
-
ff 78.5.0 esr
17. november 2020
Fixed
-
Various stability, functionality, and security fixes
QuoteSecurity Vulnerabilities fixed in Firefox ESR 78.5
- Announced November 17, 2020
- Impact high
- Products Firefox ESR
- Fixed in
-
- Firefox ESR 78.5
#CVE-2020-26951: Parsing mismatches could confuse and bypass security sanitizer for chrome privileged code
- Reporter Irvan Kurniawan (@sourc7)
- Impact high
Description
A parsing and event loading mismatch in Firefox's SVG code could have allowed load events to fire, even after sanitization. An attacker already capable of exploiting an XSS vulnerability in privileged internal pages could have used this attack to bypass our built-in sanitizer.
References
#CVE-2020-16012: Variable time processing of cross-origin images during drawImage calls
- Reporter Aleksejs Popovs
- Impact moderate
Description
When drawing a transparent image on top of an unknown cross-origin image, the Skia library
drawImagefunction took a variable amount of time depending on the content of the underlying image. This resulted in potential cross-origin information exposure of image content through timing side-channel attacks.References
#CVE-2020-26953: Fullscreen could be enabled without displaying the security UI
- Reporter Abdulrahman Alqabandi of Microsoft Browser Vulnerability Research
- Impact moderate
Description
It was possible to cause the browser to enter fullscreen mode without displaying the security UI; thus making it possible to attempt a phishing attack or otherwise confuse the user.
References
#CVE-2020-26956: XSS through paste (manual and clipboard API)
- Reporter Irvan Kurniawan (@sourc7)
- Impact moderate
Description
In some cases, removing HTML elements during sanitization would keep existing SVG event handlers and therefore lead to XSS.
References
#CVE-2020-26958: Requests intercepted through ServiceWorkers lacked MIME type restrictions
- Reporter Moti Harmats
- Impact moderate
Description
Firefox did not block execution of scripts with incorrect MIME types when the response was intercepted and cached through a ServiceWorker. This could lead to a cross-site script inclusion vulnerability, or a Content Security Policy bypass.
References
#CVE-2020-26959: Use-after-free in WebRequestService
- Reporter Bharadwaj Machiraju
- Impact moderate
Description
During browser shutdown, reference decrementing could have occured on a previously freed object, resulting in a use-after-free, memory corruption, and a potentially exploitable crash.
References
#CVE-2020-26960: Potential use-after-free in uses of nsTArray
- Reporter Zijie Zhao
- Impact moderate
Description
If the
Compact()method was called on an nsTArray, the array could have been reallocated without updating other pointers, leading to a potential use-after-free and exploitable crash.References
#CVE-2020-15999: Heap buffer overflow in freetype
- Reporter Sergei Glazunov of Google Project Zero
- Impact moderate
Description
In Freetype, if PNG images were embedded into fonts, the
Load_SBit_Pngfunction contained an integer overflow that led to a heap buffer overflow, memory corruption, and an exploitable crash.
Note: While Project Zero did discover instances of this vulnerability being exploited in the wild against Chrome, in Firefox this vulnerability is only triggerable if a rarely-used, hidden preference is toggled, and only affected Linux and Android operating systems. Other operating systems are unaffected; and Linux and Android are unaffected in the default configuration.References
#CVE-2020-26961: DoH did not filter IPv4 mapped IP Addresses
- Reporter Gabriel Corona
- Impact moderate
Description
When DNS over HTTPS is in use, it intentionally filters RFC1918 and related IP ranges from the responses as these do not make sense coming from a DoH resolver. However when an IPv4 address was mapped through IPv6, these addresses were erroneously let through, leading to a potential DNS Rebinding attack.
References
#CVE-2020-26965: Software keyboards may have remembered typed passwords
- Reporter Makoto Kato
- Impact low
Description
Some websites have a feature "Show Password" where clicking a button will change a password field into a textbook field, revealing the typed password. If, when using a software keyboard that remembers user input, a user typed their password and used that feature, the type of the password field was changed, resulting in a keyboard layout change and the possibility for the software keyboard to remember the typed password.
References
#CVE-2020-26966: Single-word search queries were also broadcast to local network
- Reporter tiebuchen
- Impact low
Description
Searching for a single word from the address bar caused an mDNS request to be sent on the local network searching for a hostname consisting of that string; resulting in an information leak.
Note: This issue only affected Windows operating systems. Other operating systems are unaffected.References
#CVE-2020-26968: Memory safety bugs fixed in Firefox 83 and Firefox ESR 78.5
- Reporter Mozilla developers and community
- Impact high
Description
Mozilla developers Steve Fink, Jason Kratzer, Randell Jesup, Christian Holler, and Byron Campen reported memory safety bugs present in Firefox 82 and Firefox ESR 78.4. Some of these bugs showed evidence of memory corruption and we presume that with enough effort some of these could have been exploited to run arbitrary code.
References
-
-
ff v83.0
17. november 2020
New
-
Firefox keeps getting faster as a result of significant updates to SpiderMonkey, our JavaScript engine, you will now experience improved page load performance by up to 15%, page responsiveness by up to 12%, and reduced memory usage by up to 8%. We have replaced part of the JavaScript engine that helps to compile and display websites for you, improving security and maintainability of the engine at the same time.
-
Firefox introduces HTTPS-Only Mode. When enabled, this new mode ensures that every connection Firefox makes to the web is secure and alerts you when a secure connection is not available. You can enable it in Firefox Preferences.
-
Pinch zooming will now be supported for our users with Windows touchscreen devices and touchpads on Mac devices. Firefox users may now use pinch to zoom on touch-capable devices to zoom in and out of webpages.
-
Picture-in-Picture now supports keyboard shortcuts for fast forwarding and rewinding videos: use the arrow keys to move forward and back 15 seconds, along with volume controls. For a list of supported commands see Support Mozilla
-
When you are presenting your screen on a video conference in Firefox, you will see our improved user interface that makes it clearer which devices or displays are being shared.
-
We’ve improved functionality and design for a number of Firefox search features:
- Selecting a search engine at the bottom of the search panel now enters search mode for that engine, allowing you to see suggestions (if available) for your search terms. The old behavior (immediately performing a search) is available with a shift-click.
- When Firefox autocompletes the URL of one of your search engines, you can now search with that engine directly in the address bar by selecting the shortcut in the address bar results.
- We’ve added buttons at the bottom of the search panel to allow you to search your bookmarks, open tabs, and history.
-
Firefox supports AcroForm, which will allow you to fill in, print, and save supported PDF forms and the PDF viewer also has a new fresh look.
-
Our users in India on the English build of Firefox will now see Pocket recommendations in their new tab featuring some of the best stories on the web. If you don’t see them, you can turn on Pocket articles in your new tab by following these steps.
-
For the recently released Apple devices built with Apple Silicon CPUs, you can use Firefox 83 and future releases without any change. This release (83) will support emulation under Apple’s Rosetta 2 that ships with macOS Big Sur. We are working toward Firefox being natively-compiled for these CPUs in a future release.
-
This is a major release for WebRender as we roll out to more Firefox users on Windows 7 and 8 as well as on macOS 10.12 to 10.15.
Fixed
-
This release also includes a number of accessibility fixes:
- Screen reader features which report paragraphs now correctly report paragraphs instead of lines in Google Docs
- When reading by word using a screen reader, words are now correctly reported when there is punctuation nearby
- The arrow keys now work correctly after tabbing in the picture-in-picture window
-
For users on macOS restoring a session with minimized windows, Firefox now uses much less power and you should see much longer battery life.
-
Various security fixes
Enterprise
Developer
-
Developers can use the scroll badge in the Page Inspector to Debug scrollable overflow. Selecting the badge highlights elements that are causing overflow and marks them with the overflow badge
Web Platform
-
This release adds support for conic gradients in CSS, helping colors to smoothly transition as you spin around the center, rather than as you progress outward from the center.
-
-
mmmh, yes. on w8.1 too.
i use the portable version and there i can only try "skip user account..."
on v5.72 and v5.73



The Firefox/Mozilla Thread
in Software
Posted
ff v78.7.1 esr
5. feb 2021
Fixed
Security fix
Prevent access to NTFS special paths that could lead to filesystem corruption.