-
Posts
2,544 -
Joined
-
Last visited
Posts posted by trium
-
-
On 12/02/2022 at 11:51, warpc0il said:
It's only when clearing Custom File and Folders that the problem occurs.
Perhaps its only by me but the cleaning of ff cache with a fews days without cleaning it takes a little bit longer (1 gb or so)
-
ublock v1.41.2
10. Feb 2022
Notes
Mozilla Add-ons Team rejected 1.41.0 and disabled the submission, and this breaks the history of uBO's versions for Firefox. See Release 1.41.0 for complete release notes for 1.41.2.
Closed as fixed:
Notable commits without an entry in the issue tracker:
-
ublock v1.41.0
08. Feb 2022
Firefox: Rejected by Mozilla Add-ons Team. The reason is that I did not provide an exact link to the origin of the hsluv-0.1.0.min.js library used by uBO to implement dark theme (uBO's About page does credit the author of the library). A README has been added to 1.41.2 to disclose the exact origin of the library.
Notes
Minimum supported browser versions has been bumped up:
- Firefox 68
-
Chromium 66
- Consequently, Opera 53
New
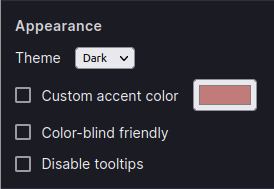
Dark mode
Support for dark mode added to the Settings pane, under the (new) Appearance section:
The new setting can be either Auto, Light, or Dark.
In addition, there is a new setting to control the accent color used by uBO throughout its user interface:
For example, changing the accent color changes the look of the popup panel:
Behavior at browser launch
A new setting in "Filter lists" pane to control whether uBO should wait for all filter lists to be loaded before unsuspending network activity.
By default, at browser launch uBO waits for all filter lists to be loaded before unsuspending network activity so as to ensure web pages are properly filtered at launch.
The new setting allows to opt out of network activity suspension at launch, i.e. allowing web pages to load without waiting for filter lists to be fully loaded, of course at the cost of potentially not filtering properly those web pages.
Closed as fixed:
Chromium-based browsers
Core
-
Logger incorrectly reporting
header=filters - Picker is broken by quotation mark in attribute
- Use "…" instead of "..."
-
Fix bad detection of unnecessary trailing
| - Unexplained popup block on streamlare
- Scrollbars appear in click2load.html
- Element Zapper denies on a specific website
- Prevent uBO from hiding html or body when matched by a generic cosmetic filter (final fix)
- Dark Mode support
Notable commits without an entry in the issue tracker:
-
Add a redirectable script that sets canRunAds true
- Related commit (contributed by @Yuki2718)
- Raise minimum versions of browsers
- Improve dealing with ambiguity in regex-based-looking network filters
- Improve google-analytics shim
- Fix regression causing regex-based filters to be case sensitive
- Add shim for FingerprintJS (aka Fingerprint v3)
- Disable the suspending of network requests when installing the extension
- Do not select background images as best candidate in picker
- Add "blockedDetails" section to troubleshooting information
- Remove "ABP X Files" from stock filter lists
- Add setting to control suspension on network activity at launch
- Make FilterJustOrigin derive from FilterOriginHitSet
-
ublock v1.40.8
11. Jan 2022
-
Fix selfie with invalid data in some circumstances (reported internally by @gwarser)
- Fix bad release 1.40.6: the previous release should have forced an invalidation of existing selfie, I overlooked this.
-
Fix selfie with invalid data in some circumstances (reported internally by @gwarser)
-
ublock v1.40.4
02. Jan 2022
Notes
This release is intended for Chromium-based browsers only.
Closed as fixed:
Chromium
Notable commits without an entry in the issue tracker:
-
-
ublock v1.40.0
22. Dec 2021
Notes:
Given that the format of compiled lists and selfie changed, this may cause a noticeable delay for the first launch after updating to 1.40.0 on less powerful devices. For a concrete example, in Firefox for Android I got ~7 seconds launch time after update to 1.40.0. Subsequent launches will be back to normal, for example on mobile I get ~790ms with selfie (and "uBlock filters -- Annoyances" enabled). On more powerful devices, this should be less noticeable if at all.
Closed as fixed:
- Inconsistent line-break in the support pane for Japanese environment
- Wrong description in Trusted site pane
- Update nobab
- Specific-generic cosmetic filter is not disabled by generichide
- "Your request URL is too long": problem with too many filters and the new "problem with filter lists" button
- Exceptions do not work when processing requests with long paths
Notable commits without an entry in the issue tracker
- Improve auto-completion in "My filters" editor
-
Store
domain=option into trie container's character buffer - Partially bring suspendTabsUntilReady out of experimental status
-
Fix potentially reporting wrong context in logger for
ghidefilters - Fine-tune static network filtering engine code
-
Wait for placeholders to be present (in
googlesyndication_adsbygoogle.js) - Create synthetic event for new windows created from external application
-
Add
window.closescriptlet - Store regex filter pattern into bidi-trie buffer
- Ignore pointless trailing *^ in network filters
- Change compiled list format to a saner block id management
- Store generic pattern string into bidi-trie buffer
- Remove classes specialized in handling single-wildcarded patterns
- Refactoring work in static network filtering engine
-
Have
getAll()returns at least one neutered Tracker object
-
ublock v1.39.2
30. Nov 2021
Closed as fixed
Notable commits without an entry in the issue tracker
-
ublock v1.39.0
Important
Fixed security issues reported by @hackvertor, see "uBlock, I exfiltrate: exploiting ad blockers with CSS".
New
A new "Report an issue on this website" icon has been added to the popup panel, to make it easier to report filter issue to volunteers maintaining filter lists. Reporting filter issues through this new feature requires a GitHub account.
A new Support pane has been added to the dashboard, to make it easy for users to share technical information about their current uBO's configuration, and consequently make it easier for volunteers to diagnose reported issues.
Closed as fixed
Chromium
- Text editing boxes have mouse location issues in higher DPIs
-
Cosmetic filters not working on many websites with "Experimental Web Platform features" in
chrome://flags- This also fixed "Security: Comments can still be used to smuggle arbitrary CSS", which was reported afterward.
Core
- [discovered by @hackvertor] Security: Cosmetic filters can make background requests using image-set() on Firefox
- uBlock GA overwrites breaking _link implementation when using a named property
- [discovered by @hackvertor] Security: Smuggle arbitrary CSS inside cosmetic uBlock filters
- [discovered by @hackvertor] Security: JavaScript URL injection allowed in query string parameter and redirection to uBlock origin urls
- Fix not highlighting cases of invalid syntax
- [patch by @pixeltris] Twitch bypass is circumvented
- Extension report website adblocking option
- [patch by @eligrey] Don't assume document.documentElement is non-null
- Add support for pseudo classes
Notable commits without an entry in the issue tracker
- Do not decode query parameter name when used as token
- Suggest network filter as best candidate by default
- Auto-escape commas in removeparam's regexes
- Simplify handling of valid HTML tags in i18n files
- Give precedence to negated types in case of ambiguity
- Fix regression in isBlockImportant()
- Add refresh-defuser scriptlet
- Add advanced setting to modify default webext flavor
- Convert fingerprint2.js scriptlet into a redirectable resource
-
-
ublock v1.38.4
Notable commits without an entry in the issue tracker
- Update twitch-videoad scriptlet (solution contibuted by @pixeltris)
-
ublock v1.38.2
Closed as fixed:
-
ublock v1.38.0
New
:matches-path(...)
New cosmetic procedural operator,
:matches-path(...). See "Add $path modifier of Adguard or any equivalents of this".Node.js
A new Node.js package will now published with every release. The package allows to import and use uBO's static and dynamic filtering engines into Node.js. This is currently minimal and a first iteration, and issues regarding the Node.js package are accepted in order to improve usability of uBO's filtering engines in a Node.js package. The ability to run code from a Node.js package also opens the door to have test coverage in uBO.
For now the package can be downloaded and unzipped locally. Once installed, you can execute
node testin the root of the package to verify that the static network filtering engine works properly. For usage, refer to thetest.js, orublock.jsused in Cliqz's benchmark.Since I have little experience with dealing with Node.js environment/packages, thanks to @mjethani for assistance.
Removed
The setting "Prevent WebRTC from leaking local IP addresses" has been removed since it is no longer necessary in modern browsers, except for Firefox for Android where the issue is still present.
Closed as fixed:
- Remove WebRTC leak prevention
- $removeparam doesn't work well with UrlEncoded gb2312 Chinese word
- Scriptlets don't work randomly in Firefox
- Security: comments can be used to smuggle url() functions into css values
- Prevent uBO from hiding html or body when matched by a generic cosmetic filter
- On Android Popup Overlays [or Underlays] On-Screen Navigation Buttons
- Add $path modifier of Adguard or any equivalents of this
- The overview panel will not show everything if the uBO's icon is placed in the Firefox overflow menu
- [patch by @vtriolet] TypeError in noscript-spoof scriptlet with invalid meta refresh URL
- TypeError when trying to use element picker on plaintext resource
-
Split out core functionality into separate module
- This is of course an ongoing work for the foreseeable future, but the concrete goal sought in the issue has been reached, i.e. the static network filtering engine can be used as a nodejs module with no external dependencies.
- Since uBO's codebase now uses JS modules, the minimum version of supported browsers has been increased to Chromium 61, Firefox 60, and Opera 48.
Notable commits without an entry in the issue tracker
- Better lookup all elements under mouse cursor in element picker
- Add visual hint to grab area of element picker dialog
- Add no-xhr-if scriptlet
- Refactor hntrie to avoid the need for boundary cells
- Fix bad test in WASM version of HNTrieContainer
- Export the rule-based filtering engines to the nodejs package
- Rewrite logical expressions for ESLint
- [patch by @mjethani] Add Makefile
- [patch by @mjethani] Make uAssets a submodule
- Ensure compiled sections are ordered in ascending id
-
Fix handling of some procedural cosmetic filters with explicit
:scope
-
ff v.91.6.0 esr
08. february 2022
Fixed
-
Various stability, functionality, and security fixes
QuoteSecurity Vulnerabilities fixed in Firefox ESR 91.6
- Announced February 8, 2022
- Impact high
- Products Firefox ESR
- Fixed in
-
- Firefox ESR 91.6
#CVE-2022-22753: Privilege Escalation to SYSTEM on Windows via Maintenance Service
- Reporter Seb Patane
- Impact high
Description
A Time-of-Check Time-of-Use bug existed in the Maintenance (Updater) Service that could be abused to grant Users write access to an arbitrary directory. This could have been used to escalate to SYSTEM access.
This bug only affects Firefox on Windows. Other operating systems are unaffected.References
#CVE-2022-22754: Extensions could have bypassed permission confirmation during update
- Reporter Rob Wu
- Impact high
Description
If a user installed an extension of a particular type, the extension could have auto-updated itself and while doing so, bypass the prompt which grants the new version the new requested permissions.
References
#CVE-2022-22756: Drag and dropping an image could have resulted in the dropped object being an executable
- Reporter Abdulrahman Alqabandi
- Impact moderate
Description
If a user was convinced to drag and drop an image to their desktop or other folder, the resulting object could have been changed into an executable script which would have run arbitrary code after the user clicked on it.
References
#CVE-2022-22759: Sandboxed iframes could have executed script if the parent appended elements
- Reporter Johan Carlsson
- Impact moderate
Description
If a document created a sandboxed iframe without
allow-scripts, and subsequently appended an element to the iframe's document that e.g. had a JavaScript event handler - the event handler would have run despite the iframe's sandbox.References
#CVE-2022-22760: Cross-Origin responses could be distinguished between script and non-script content-types
- Reporter Luan Herrera
- Impact moderate
Description
When importing resources using Web Workers, error messages would distinguish the difference between
application/javascriptresponses and non-script responses. This could have been abused to learn information cross-origin.References
#CVE-2022-22761: frame-ancestors Content Security Policy directive was not enforced for framed extension pages
- Reporter Mart Gil Robles (Mart at FlowCrypt)
- Impact moderate
Description
Web-accessible extension pages (pages with a moz-extension:// scheme) were not correctly enforcing the frame-ancestors directive when it was used in the Web Extension's Content Security Policy.
References
#CVE-2022-22763: Script Execution during invalid object state
- Reporter Mozilla Fuzzing Team
- Impact moderate
Description
When a worker is shutdown, it was possible to cause script to run late in the lifecycle, at a point after where it should not be possible.
References
#CVE-2022-22764: Memory safety bugs fixed in Firefox 97 and Firefox ESR 91.6
- Reporter Mozilla developers and community
- Impact high
Description
Mozilla developers and community members Paul Adenot and the Mozilla Fuzzing Team reported memory safety bugs present in Firefox 96 and Firefox ESR 91.5. Some of these bugs showed evidence of memory corruption and we presume that with enough effort some of these could have been exploited to run arbitrary code.
References
-
-
ff v97.0
08. february 2022
New
-
Firefox now supports and displays the new style of scrollbars on Windows 11.
Fixed
-
On macOS, we’ve made improvements to system font loading which makes opening and switching to new tabs faster in certain situations.
-
Various security fixes
Changed
-
On February 8, we will be expiring the 18 colorway themes of Firefox version 94. This signals the end of a special, limited-time feature set. However, you can hold onto your favorite colorway, as long as you’re using it on the expiration date. In other words, if a colorway is “enabled” in the add-ons manager, that colorway is yours forever. Read more about colorway updates here.
-
Support for directly generating PostScript for printing on Linux has been removed. Printing to PostScript printers still remains a supported option, however.
Enterprise
-
Various bug fixes and new policies have been implemented in the latest version of Firefox. You can find more information in the Firefox for Enterprise 97 Release Notes.
Developer
unresolved
-
Users running WebRoot SecureAnywhere Antivirus may experience impaired functionality when upgrading to Firefox 97. Closing WebRoot will allow Firefox to resume normal operation.
-
-
ff v91.5.1 esr
27. january 2022
Fixed
-
Fixed an issue that allowed unexpected data to be submitted in some of our search telemetry (bug 1752317)
-
-
ff v96.0.3
27. january 2022
Fixed
-
Fixed an issue that allowed unexpected data to be submitted in some of our search telemetry (bug 1752317)
-
-
ff v96.0.2
20. january 2022
Fixed
-
Fixed an issue that caused tab height to display inconsistently on Linux when audio was played (bug 1714276)
-
Fixed an issue that caused Lastpass dropdowns to appear blank in Private Browsing mode (bug 1748158)
-
Fixed a crash encountered when resizing a Facebook app (bug 1746084)
-
-
ff v96.0.1
14. january 2022
Fixed
-
Addresses proxy rule exceptions not working on Windows systems when "Use system proxy settings" is set (bug 1749501)
-
Improvements to make the parsing of content-length headers more robust (bug 1749957)
-
-
ff v91.5.0 esr
11. january 2022
Fixed
-
Various stability, functionality, and security fixes
QuoteSecurity Vulnerabilities fixed in Firefox ESR 91.5
- Announced January 11, 2022
- Impact high
- Products Firefox ESR
- Fixed in
-
- Firefox ESR 91.5
#CVE-2022-22746: Calling into reportValidity could have lead to fullscreen window spoof
- Reporter Irvan Kurniawan
- Impact high
Description
A race condition could have allowed bypassing the fullscreen notification which could have lead to a fullscreen window spoof being unnoticed.
This bug only affects Thunderbird for Windows. Other operating systems are unaffected.References
#CVE-2022-22743: Browser window spoof using fullscreen mode
- Reporter Irvan Kurniawan
- Impact high
Description
When navigating from inside an iframe while requesting fullscreen access, an attacker-controlled tab could have made the browser unable to leave fullscreen mode.
References
#CVE-2022-22742: Out-of-bounds memory access when inserting text in edit mode
- Reporter Irvan Kurniawan
- Impact high
Description
When inserting text while in edit mode, some characters might have lead to out-of-bounds memory access causing a potentially exploitable crash.
References
#CVE-2022-22741: Browser window spoof using fullscreen mode
- Reporter Irvan Kurniawan
- Impact high
Description
When resizing a popup while requesting fullscreen access, the popup would have become unable to leave fullscreen mode.
References
#CVE-2022-22740: Use-after-free of ChannelEventQueue::mOwner
- Reporter bo13oy of Cyber Kunlun Lab
- Impact high
Description
Certain network request objects were freed too early when releasing a network request handle. This could have lead to a use-after-free causing a potentially exploitable crash.
References
#CVE-2022-22738: Heap-buffer-overflow in blendGaussianBlur
- Reporter Atte Kettunen
- Impact high
Description
Applying a CSS filter effect could have accessed out of bounds memory. This could have lead to a heap-buffer-overflow causing a potentially exploitable crash.
References
#CVE-2022-22737: Race condition when playing audio files
- Reporter bo13oy of Cyber Kunlun Lab
- Impact high
Description
Constructing audio sinks could have lead to a race condition when playing audio files and closing windows. This could have lead to a use-after-free causing a potentially exploitable crash.
References
#CVE-2021-4140: Iframe sandbox bypass with XSLT
- Reporter Peter Van der Beken
- Impact high
Description
It was possible to construct specific XSLT markup that would be able to bypass an iframe sandbox.
References
#CVE-2022-22748: Spoofed origin on external protocol launch dialog
- Reporter Alesandro Ortiz
- Impact moderate
Description
Malicious websites could have confused Thunderbird into showing the wrong origin when asking to launch a program and handling an external URL protocol.
References
#CVE-2022-22745: Leaking cross-origin URLs through securitypolicyviolation event
- Reporter Jannis Rautenstrauch
- Impact moderate
Description
Securitypolicyviolation events could have leaked cross-origin information for frame-ancestors violations
References
#CVE-2022-22744: The 'Copy as curl' feature in DevTools did not fully escape website-controlled data, potentially leading to command injection
- Reporter Mattias Jacobsson
- Impact moderate
Description
The constructed curl command from the "Copy as curl" feature in DevTools was not properly escaped for PowerShell. This could have lead to command injection if pasted into a Powershell prompt.
This bug only affects Firefox for Windows. Other operating systems are unaffected.References
#CVE-2022-22747: Crash when handling empty pkcs7 sequence
- Reporter Tavis Ormandy
- Impact low
Description
After accepting an untrusted certificate, handling an empty pkcs7 sequence as part of the certificate data could have lead to a crash. This crash is believed to be unexploitable.
References
#CVE-2022-22739: Missing throttling on external protocol launch dialog
- Reporter Alesandro Ortiz
- Impact low
Description
Malicious websites could have tricked users into accepting launching a program to handle an external URL protocol.
References
#CVE-2022-22751: Memory safety bugs fixed in Firefox 96 and Firefox ESR 91.5
- Reporter Mozilla developers and community
- Impact high
Description
Mozilla developers Calixte Denizet, Kershaw Chang, Christian Holler, Jason Kratzer, Gabriele Svelto, Tyson Smith, Simon Giesecke, and Steve Fink reported memory safety bugs present in Firefox 95 and Firefox ESR 91.4. Some of these bugs showed evidence of memory corruption and we presume that with enough effort some of these could have been exploited to run arbitrary code.
References
-
-
ff v96.0
11. january 2022
New
-
We’ve made significant improvements in noise-suppression and auto-gain-control as well as slight improvements in echo-cancellation to provide you with a better overall experience.
-
We’ve also significantly reduced main-thread load.
-
When printing, you can now choose to print only the odd/even pages.
Fixed
-
On macOS, command-clicking links in Gmail now opens them in a new tab as expected.
-
Our newest release fixes an issue where video intermittently drops SSRC.
-
It also fixes an issue where WebRTC downgrades screen sharing resolution to provide you with a clearer browsing experience.
-
Plus, we’ve fixed video quality degradation issues on certain sites.
-
Detached video in fullscreen on macOS has been temporarily disabled to avoid some issues with corruption, brightness changes, missing subtitles and high cpu usage.
-
Various security fixes
Enterprise
-
Various bug fixes and new policies have been implemented in the latest version of Firefox. You can find more information in the Firefox for Enterprise 96 Release Notes.
Developer
-
Firefox for Linux changes the shortcut key for "Select All" from
Alt-AtoCtrl-Afor solving web-compatibility and avoiding conflict with access keys. If you want to keep using Emacs like key bindings, e.g., you configured your GTK settings to useCtrl-Aas a shortcut key for moving caret to beginning of a line, you must changeui.key.textcontrol.prefer_native_key_bindings_over_builtin_shortcut_key_definitionsandui.key.use_select_all_in_single_line_editorfromabout:config. Currently, these are disabled by default but will be enabled by default in a future release.
Web Platform
-
The Web Locks API landed. This allows scripts running in different service workers or tabs to coordinate with each other.
-
WebRTC library updated, bringing improved audio and video features for web conferencing applications.
-
Added CSS color-scheme support to allow web pages to indicate which color schemes they can be rendered with (for example, operating system dark mode).
-
-
hallo timon,
nach dem, was ich so gelesen habe, glaube ich nicht, dass du deine lizenz auf die ccleaner-app für android übertragen kannst.
ich denke, bei der windows-version kannst du ccleaner pro nur 3 windows-computern verwenden und auf der android-version kannst du ccleaner auf mehr als 1 android gerät verwenden.
QuoteWe don't include CCleaner for Android, Chromebooks, and Kindle Fire in the Professional Plus bundle.
QuoteThe CCleaner Professional Plus bundle works on up to 3 computers
QuoteYour CCleaner Android Pro subscription is connected to your Google account, and activates automatically on all devices connected to your account when you install the app. If the premium features are not automatically unlocked, you can activate an existing subscription in your CCleaner Android settings.
-
ff v91.4.1 esr
16. dec 2021
Fixed
-
Fixed frequent MOZILLA_PKIX_ERROR_OCSP_RESPONSE_FOR_CERT_MISSING error messages when trying to connect to various microsoft.com domains (bug 1745600)
-
-
ff v95.0.2
19. dec 2021
Fixed
-
Addresses frequent crashes experienced by users with C/E/Z-Series "Bobcat" CPUs running on Windows 7, 8, and 8.1.
-





Deletion of "Custom File and Folders" takes 10x as long as Delete in Explorer
in CCleaner Bug Reporting
Posted
Sorry, not 1 gb.
Some 100's if mb :-).
perhaps its slow because it delete every single entry - step by step instead of cleaning all entrys in one step (secure deletion...)