-
Posts
2,544 -
Joined
-
Last visited
Posts posted by trium
-
-
-
ublock v1.42.0
github-actions released this
30. Mar 2022
Fixes:
-
Handle
picture > sourceelements in element picker - Use a better value to mark end of sequence of tokens
- Remove MVPS from stock lists due to inactivity
- A way to fix serious filter issues as soon as possible
- Add command to toggle cosmetic filtering
- Prevent unset minimal width for popup panel
Notable commits without an entry in the issue tracker:
-
Handle
-
-
-
ublock v1.41.4
github-actions released this
16. Feb 2022
Notes
As per various feedback, the new setting "Suspend network activity until all filter lists are loaded" is now unchecked by default in Chromium-based browsers. You will have to explicitly enable it to restore the attempt at mitigating Chromium-based browsers inability to reliably block network requests at launch.
Closed as fixed:
-
nicki - wegen dir (1986)
-
nicki - koana war so wie du (1989)
-
nicki - mit dir des wär mei leben (1989)
-
juliane werding - am tag als conny kramer starb (1972)
-
ff v104.0.2
06. sept 2022
Fixed
-
Fixed a bug making it impossible to use touch or a stylus to drag the scrollbar on pages (bug 1787361).
-
Fixed an issue causing some users to crash in out-of-memory conditions (bug 1774155).
-
Fixed an issue that would sometimes affect video & audio playback when loaded via a cross-origin iframe
srcattribute (bug 1781759). -
Fixed an issue that would sometimes affect video & audio playback when served with Content-Security-Policy:
sandbox(bug 1781063).
-
-
ff v104.0.1
30. august 2022
Fixed
-
Addresses an issue with Youtube video playback that was affecting some users.
-
-
ff v102.2.0 esr
23. august 2022
Fixed
-
Various stability, functionality, and security fixes.
QuoteSecurity Vulnerabilities fixed in Firefox ESR 102.2
- Announced August 23, 2022
- Impact high
- Products Firefox ESR
- Fixed in
-
- Firefox ESR 102.2
#CVE-2022-38472: Address bar spoofing via XSLT error handling
- Reporter Armin Ebert
- Impact high
Description
An attacker could have abused XSLT error handling to associate attacker-controlled content with another origin which was displayed in the address bar. This could have been used to fool the user into submitting data intended for the spoofed origin.
References
#CVE-2022-38473: Cross-origin XSLT Documents would have inherited the parent's permissions
- Reporter Armin Ebert
- Impact high
Description
A cross-origin iframe referencing an XSLT document would inherit the parent domain's permissions (such as microphone or camera access).
References
#CVE-2022-38476: Data race and potential use-after-free in PK11_ChangePW
- Reporter Marian Laza
- Impact low
Description
A data race could occur in the
PK11_ChangePWfunction, potentially leading to a use-after-free vulnerability. In Firefox, this lock protected the data when a user changed their master password.References
#CVE-2022-38477: Memory safety bugs fixed in Firefox 104 and Firefox ESR 102.2
- Reporter Mozilla developers and community
- Impact high
Description
Mozilla developer Nika Layzell and the Mozilla Fuzzing Team reported memory safety bugs present in Firefox 103 and Firefox ESR 102.1. Some of these bugs showed evidence of memory corruption and we presume that with enough effort some of these could have been exploited to run arbitrary code.
References
#CVE-2022-38478: Memory safety bugs fixed in Firefox 104, Firefox ESR 102.2, and Firefox ESR 91.13
- Reporter Mozilla developers and community
- Impact high
Description
Members the Mozilla Fuzzing Team reported memory safety bugs present in Firefox 103, Firefox ESR 102.1, and Firefox ESR 91.12. Some of these bugs showed evidence of memory corruption and we presume that with enough effort some of these could have been exploited to run arbitrary code.
References
-
-
ff v104.0
23. august 2022
New
-
Subtitles are now available for Disney+ in Picture-in-Picture.
-
Firefox now supports both the
scroll-snap-stopproperty as well asre-snapping. You can use the scroll-snap-stop property's always and normal values to specify whether or not to pass the snap points, even when scrolling fast.Re-snappingtries to keep the last snap position after any content/layout changes. -
The Firefox profiler can analyze power usage of a website (Apple M1 and Windows 11 only).
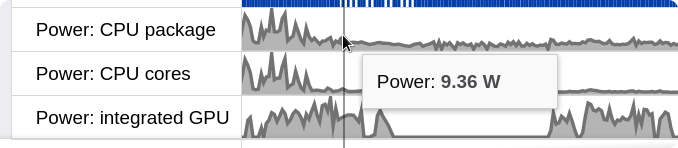
-
The Firefox UI itself will now be throttled for performance and battery usage when minimized or occluded, in the same way background tabs are.
Fixed
-
Highlight color is preserved correctly after typing
Enterin the mail composer of Yahoo Mail and Outlook. -
After bypassing the https only error page navigating back would take you to the error page that was previously dismissed. Back now takes you to the previous site that was visited.
-
Paste unformatted shortcut (shift+ctrl/cmd+v) now works in plain text contexts, such as input and text area.
-
Various security fixes.
Enterprise
-
Various bug fixes and new policies have been implemented in the latest version of Firefox. You can find more information in the Firefox for Enterprise 104 Release Notes.
Developer
-
-
ff v91.13.0 esr
23. august 2022
Fixed
-
Various stability, functionality, and security fixes.
QuoteSecurity Vulnerabilities fixed in Firefox ESR 91.13
- Announced August 23, 2022
- Impact high
- Products Firefox ESR
- Fixed in
-
- Firefox ESR 91.13
#CVE-2022-38472: Address bar spoofing via XSLT error handling
- Reporter Armin Ebert
- Impact high
Description
An attacker could have abused XSLT error handling to associate attacker-controlled content with another origin which was displayed in the address bar. This could have been used to fool the user into submitting data intended for the spoofed origin.
References
#CVE-2022-38473: Cross-origin XSLT Documents would have inherited the parent's permissions
- Reporter Armin Ebert
- Impact high
Description
A cross-origin iframe referencing an XSLT document would inherit the parent domain's permissions (such as microphone or camera access).
References
#CVE-2022-38478: Memory safety bugs fixed in Firefox 104, Firefox ESR 102.2, and Firefox ESR 91.13
- Reporter Mozilla developers and community
- Impact high
Description
Members the Mozilla Fuzzing Team reported memory safety bugs present in Firefox 103, Firefox ESR 102.1, and Firefox ESR 91.12. Some of these bugs showed evidence of memory corruption and we presume that with enough effort some of these could have been exploited to run arbitrary code.
References
-
-
ff v103.0.2
09. august 2022
Fixed
-
Fixed menu shortcuts for users of the JAWS screen reader.
-
Fixed an occasional non-overridable certificate error when accessing device configuration pages.
-
Fixed an issue with Picture-in-Picture displaying in fullscreen on macOS.
-
-
-
On 29/07/2022 at 07:29, brendenjacobson said:
My cores are not running at 3.6GHz. The first 6 are really running at 4.5 to 4.9
can i ask you something?
laptop or desktop?
power plan settings? balance or top performance?
need your pc really 6 cores x 2 = 12 threads x 4,9 ghz highspeed of "performance cores"? and 4 x 3.6 ghz of efficient cores?
this is a lot of computing power...
i dont know if hyperthreading is additionally to the real cores and ghz or not...
- > with top performance are this 58,8 ghz + 14.4 ghz = 73.2 ghz
-> with balance are this 44.4 ghz + 11.2 ghz = 55.6 ghz
without hyperthreading:
-> with top performance are this 29.4 ghz + 14.4 ghz = 43.8 ghz
-> with balance are this 22.2 ghz + 11.2 ghz = 33.4 ghz
performance core base - 3.7 ghz
performance core turbo - 4.9 ghz
efficient core base - 2.8 ghz
efficient core turbo - 3.6 ghz
-
w11 is not the problem ;-)
as i read... ms will w11 updating to w12 perhaps in 2024 and after this every 3 years a "major update" with a "new" windows-version
-
ff v103.0.1
01. august 2022
New
-
Enabled hardware acceleration on newer AMD cards.
Fixed
-
Fixed a crash on Firefox shutdown caused by a bug in the audio manager.
-
-
ff v103.0
26. july 2022
New
-
Improved responsiveness on macOS during periods of high CPU load by switching to a modern lock API.
-
Do you always forget something? Required fields are now highlighted in PDF forms.
-
Improved performance on high-refresh rate monitors (120Hz+).
-
Enjoying Picture-in-Picture subtitles feature? It just got better: you can now change subtitles font size directly from the PiP window. Additionally, PiP subtitles are now available at Funimation, Dailymotion, Tubi, Hotstar, and SonyLIV.
-
Buttons in the Tabs toolbar can now be reached with Tab, Shift+Tab, and Arrow keys. View this article for additional details.
-
Windows' "Make text bigger" accessibility setting now affects all the UI and content pages, rather than only applying to system font sizes.
-
Rejoice! You can now conveniently access Firefox, which will now be pinned to the Windows taskbar during installation on Windows 10 and 11. (This will also allow for Firefox to be launched quicker after installing.)
Fixed
-
Non-breaking spaces are now preserved—preventing automatic line breaks—when copying text from a form control.
-
Fixed WebGL performance issues on NVIDIA binary drivers via DMA-Buf on Linux.
-
Fixed an issue in which Firefox startup could be significantly slowed down by the processing of Web content local storage. This had the greatest impact on users with platter hard drives and significant local storage.
-
Various security fixes.
Changed
-
Removed a configuration option to allow SHA-1 signatures in certificates: SHA-1 signatures in certificates—long since determined to no longer be secure enough—are now not supported.
Developer
Web Platform
-
Your information now has increased protection from online tracking via Total Cookie Protection enabled by default. All third-party cookies are now isolated into partitioned storage.
-
-
ff v91.12.0 esr
26. july 2022
Fixed
-
Various stability, functionality, and security fixes.
QuoteSecurity Vulnerabilities fixed in Firefox ESR 91.12
- Announced July 26, 2022
- Impact moderate
- Products Firefox ESR
- Fixed in
-
- Firefox ESR 91.12
#CVE-2022-36319: Mouse Position spoofing with CSS transforms
- Reporter Irvan Kurniawan
- Impact moderate
Description
When combining CSS properties for overflow and transform, the mouse cursor could interact with different coordinates than displayed.
References
#CVE-2022-36318: Directory indexes for bundled resources reflected URL parameters
- Reporter Gijs Kruitbosch
- Impact moderate
Description
When visiting directory listings for
chrome://URLs as source text, some parameters were reflected.References
-
-
ff v102.1.0 esr
26. july 2022
Fixed
-
Various stability, functionality, and security fixes.
QuoteSecurity Vulnerabilities fixed in Firefox ESR 102.1
- Announced July 26, 2022
- Impact moderate
- Products Firefox ESR
- Fixed in
-
- Firefox ESR 102.1
#CVE-2022-36319: Mouse Position spoofing with CSS transforms
- Reporter Irvan Kurniawan
- Impact moderate
Description
When combining CSS properties for overflow and transform, the mouse cursor could interact with different coordinates than displayed.
References
#CVE-2022-36318: Directory indexes for bundled resources reflected URL parameters
- Reporter Gijs Kruitbosch
- Impact moderate
Description
When visiting directory listings for
chrome://URLs as source text, some parameters were reflected.References
#CVE-2022-36314: Opening local <code>.lnk</code> files could cause unexpected network loads
- Reporter akucybersec
- Impact moderate
Description
When opening a Windows shortcut from the local filesystem, an attacker could supply a remote path that would lead to unexpected network requests from the operating system.
This bug only affects Firefox for Windows. Other operating systems are unaffected.*References
#CVE-2022-2505: Memory safety bugs fixed in Firefox 103 and 102.1
- Reporter Mozilla developers and community
- Impact high
Description
Mozilla developers and the Mozilla Fuzzing Team reported memory safety bugs present in Firefox 102. Some of these bugs showed evidence of memory corruption and we presume that with enough effort some of these could have been exploited to run arbitrary code.
References
-
-
ff v102.0.1
06. july 2022
Fixed
-
Fixed bookmark shortcut creation by dragging to Windows File Explorer and dropping partially broken (bug 1774683)
-
Fixed bookmarks sidebar flashing white when opened in dark mode (bug 1776157)
-
Fixed multilingual spell checking not working with content in both English and a non-Latin alphabet (bug 1773802)
-
Developer tools: Fixed an issue where the console output keep getting scrolled to the bottom when the last visible message is an evaluation result (bug 1776262)
-
Fixed Delete cookies and site data when Firefox is closed checkbox getting disabled on startup (bug 1777419)
-
Various stability fixes
-
-
ad to ff v102.0 esr
QuoteSecurity Vulnerabilities fixed in Firefox 102
- Announced June 28, 2022
- Impact high
- Products Firefox
- Fixed in
-
- Firefox 102
Note: While Bug 1771084 does not represent a specific vulnerability that was fixed, we recommend anyone rebasing patches to include it. 102 branch: Patch 1 and 2. 91 Branch: Patch 1 and 2 (Despite saying Parts 2 and 3, there is no Part 1)
#CVE-2022-34479: A popup window could be resized in a way to overlay the address bar with web content
- Reporter Irvan Kurniawan
- Impact high
Description
A malicious website that could create a popup could have resized the popup to overlay the address bar with its own content, resulting in potential user confusion or spoofing attacks.
This bug only affects Firefox for Linux. Other operating systems are unaffected.References
#CVE-2022-34470: Use-after-free in nsSHistory
- Reporter Armin Ebert
- Impact high
Description
Navigations between XML documents may have led to a use-after-free and potentially exploitable crash.
References
#CVE-2022-34468: CSP sandbox header without `allow-scripts` can be bypassed via retargeted javascript: URI
- Reporter Armin Ebert
- Impact high
Description
An iframe that was not permitted to run scripts could do so if the user clicked on a
javascript:link.References
#CVE-2022-34482: Drag and drop of malicious image could have led to malicious executable and potential code execution
- Reporter Attila Suszter
- Impact moderate
Description
An attacker who could have convinced a user to drag and drop an image to a filesystem could have manipulated the resulting filename to contain an executable extension, and by extension potentially tricked the user into executing malicious code. While very similar, this is a separate issue from CVE-2022-34483.
References
#CVE-2022-34483: Drag and drop of malicious image could have led to malicious executable and potential code execution
- Reporter Eduardo Braun Prado
- Impact moderate
Description
An attacker who could have convinced a user to drag and drop an image to a filesystem could have manipulated the resulting filename to contain an executable extension, and by extension potentially tricked the user into executing malicious code. While very similar, this is a separate issue from CVE-2022-34482.
References
#CVE-2022-34476: ASN.1 parser could have been tricked into accepting malformed ASN.1
- Reporter Gustavo Grieco
- Impact moderate
Description
ASN.1 parsing of an indefinite SEQUENCE inside an indefinite GROUP could have resulted in the parser accepting malformed ASN.1.
References
#CVE-2022-34481: Potential integer overflow in ReplaceElementsAt
- Reporter Ronald Crane
- Impact moderate
Description
In the
nsTArray_Impl::ReplaceElementsAt()function, an integer overflow could have occurred when the number of elements to replace was too large for the container.References
#CVE-2022-34474: Sandboxed iframes could redirect to external schemes
- Reporter Amazon Malvertising Team
- Impact moderate
Description
Even when an iframe was sandboxed with
allow-top-navigation-by-user-activation, if it received a redirect header to an external protocol the browser would process the redirect and prompt the user as appropriate.References
#CVE-2022-34469: TLS certificate errors on HSTS-protected domains could be bypassed by the user on Firefox for Android
- Reporter Peter Gerber
- Impact moderate
Description
When a TLS Certificate error occurs on a domain protected by the HSTS header, the browser should not allow the user to bypass the certificate error. On Firefox for Android, the user was presented with the option to bypass the error; this could only have been done by the user explicitly.
This bug only affects Firefox for Android. Other operating systems are unaffected.References
#CVE-2022-34471: Compromised server could trick a browser into an addon downgrade
- Reporter Rob Wu
- Impact moderate
Description
When downloading an update for an addon, the downloaded addon update's version was not verified to match the version selected from the manifest. If the manifest had been tampered with on the server, an attacker could trick the browser into downgrading the addon to a prior version.
References
#CVE-2022-34472: Unavailable PAC file resulted in OCSP requests being blocked
- Reporter Laurent Bigonville
- Impact moderate
Description
If there was a PAC URL set and the server that hosts the PAC was not reachable, OCSP requests would have been blocked, resulting in incorrect error pages being shown.
References
#CVE-2022-34478: Microsoft protocols can be attacked if a user accepts a prompt
- Reporter Gijs
- Impact moderate
Description
The
ms-msdt,search, andsearch-msprotocols deliver content to Microsoft applications, bypassing the browser, when a user accepts a prompt. These applications have had known vulnerabilities, exploited in the wild (although we know of none exploited through Firefox), so in this release Firefox has blocked these protocols from prompting the user to open them.
This bug only affects Firefox on Windows. Other operating systems are unaffected.References
#CVE-2022-2200: Undesired attributes could be set as part of prototype pollution
- Reporter Manfred Paul via Trend Micro's Zero Day Initiative
- Impact moderate
Description
If an object prototype was corrupted by an attacker, they would have been able to set undesired attributes on a JavaScript object, leading to privileged code execution.
References
#CVE-2022-34480: Free of uninitialized pointer in lg_init
- Reporter Ronald Crane
- Impact low
Description
Within the
lg_init()function, if several allocations succeed but then one fails, an uninitialized pointer would have been freed despite never being allocated.References
#CVE-2022-34477: MediaError message property leaked information on cross-origin same-site pages
- Reporter jannis
- Impact low
Description
The MediaError message property should be consistent to avoid leaking information about cross-origin resources; however for a same-site cross-origin resource, the message could have leaked information enabling XS-Leaks attacks.
References
#CVE-2022-34475: HTML Sanitizer could have been bypassed via same-origin script via use tags
- Reporter Gareth Heyes
- Impact low
Description
SVG
<use>tags that referenced a same-origin document could have resulted in script execution if attacker input was sanitized via the HTML Sanitizer API. This would have required the attacker to reference a same-origin JavaScript file containing the script to be executed.References
#CVE-2022-34473: HTML Sanitizer could have been bypassed via use tags
- Reporter Armin Ebert
- Impact low
Description
The HTML Sanitizer should have sanitized the
hrefattribute of SVG<use>tags; however it incorrectly did not sanitizexlink:hrefattributes.References
#CVE-2022-34484: Memory safety bugs fixed in Firefox 102 and Firefox ESR 91.11
- Reporter Mozilla developers and community
- Impact high
Description
The Mozilla Fuzzing Team reported potential vulnerabilities present in Firefox 101 and Firefox ESR 91.10. Some of these bugs showed evidence of JavaScript prototype or memory corruption and we presume that with enough effort some of these could have been exploited to run arbitrary code.
References
#CVE-2022-34485: Memory safety bugs fixed in Firefox 102
- Reporter Mozilla developers and community
- Impact moderate
Description
Mozilla developers Bryce Seager van Dyk and the Mozilla Fuzzing Team reported potential vulnerabilities present in Firefox 101. Some of these bugs showed evidence of memory corruption and we presume that with enough effort some of these could have been exploited to run arbitrary code.
References



ublock users
in Software
Posted
ublock v1.42.4
github-actions released this
06. Apr 2022
Fixes: